Deep dive into the cryptographic foundations, system components, and privacy guarantees of the Birthmark Standard.
Existing solutions like C2PA embed authentication metadata directly in image files. When images are converted, cropped, or shared on social media, this metadata is stripped—making authentication useless for 95% of real-world image distribution. The Birthmark Standard stores authentication records on an independent blockchain, surviving all forms of metadata loss.
Function: Generate cryptographic proof that specific camera hardware captured specific image data
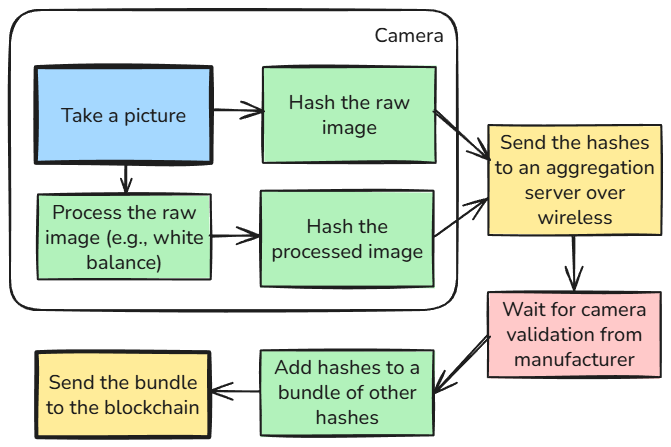
Key Innovation: Raw sensor data is hashed before Image Signal Processor (ISP) manipulation. This occurs in parallel with normal image processing via DMA, causing zero user-facing delay.
NUC Hash Permanence: The NUC hash used for camera validation is captured once during manufacturing and stored permanently in the Secure Element. This is separate from the camera's live NUC calibration used for image correction.
Function: Receive authentication submissions from cameras and editing software, validate through manufacturer/developer authorities, post to Birthmark Media Registry
Technology Stack: Python FastAPI (async), PostgreSQL (submission records), Redis (queue management)
Function: Reference implementation of manufacturer validation server that verifies camera tokens without seeing image content
Architecture: Consortium blockchain operated by the Media Validation Network—a coalition of journalism, fact-checking, and press freedom organizations. Individual image hashes are stored directly on-chain.
Storing individual hashes directly and distributing trust across mission-aligned organizations solves data availability problems. If any single Submission Server disappears, the Registry remains fully functional and queryable.
At the moment of image capture, a secure chip in the camera creates an unforgeable digital signature before the image is even processed.
Result: A bundle containing both image hashes, timestamp, and optional location hash—ready to be sent to the aggregation server for validation and blockchain recording.
Click to view full size
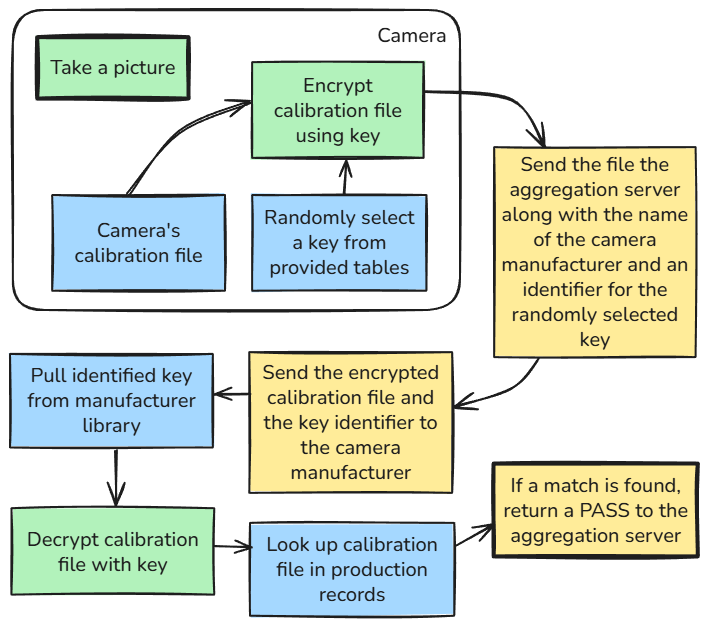
Click to view full size - Shows separation of concerns: manufacturer validates camera, never sees image content
The manufacturer confirms that images come from real cameras without being able to see what photographers are capturing or track individual cameras.
Anyone can verify an image's authenticity by checking the blockchain record—no corporate gatekeepers or subscription services required.
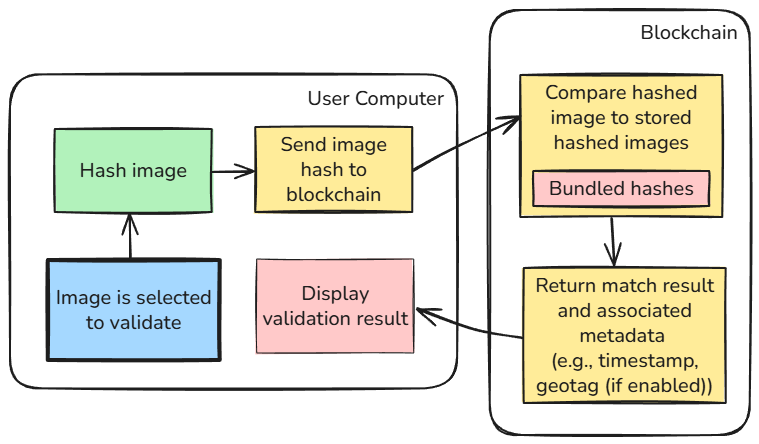
Click to view full size - User verification happens client-side
✓ "One of my cameras authenticated a photo"
✗ Which specific camera (table/index shared by thousands)
✗ Image content or hash
✗ When photo was taken
✗ Where photo was taken
✗ Which Submission Server received it
✓ Image hash (to submit to Registry)
✓ Camera certificate table/index (not camera identity)
✓ Manufacturer validation result (PASS/FAIL)
✗ Which specific camera (table shared by ~12,000 cameras)
✗ NUC hash (encrypted, cannot decrypt without key)
✗ Image content
✓ Image hashes (SHA-256, not reversible)
✓ Modification levels
✓ Authority IDs
✓ Timestamps (when Submission Server processed, not capture time)
✗ Image content
✗ Specific camera identity or photographer identity
✓ "This hash was authenticated by this manufacturer on this date"
✗ Who took the photo
✗ Where specifically (only if GPS-enabled version exists and they have that image)
✗ Which specific camera unit
Source Protection: Certificate references stored in the Registry require manufacturer cooperation to trace to specific devices, and even then require possession of the original image to identify relevant records. This architecture prevents fishing expeditions and protects source confidentiality by design.
Risk: Server manipulates submissions or goes offline
Mitigation: All data on Registry, server is stateless relay. Spin up new server, continues from blockchain state. Multiple servers can operate simultaneously.
Protection: Supermajority (67%) needed for malicious action—would need 7 of 10 journalism organizations to collude. Coalition Members have reputational stake in integrity. Media producers excluded, reducing conflict of interest.
Protection: Legal compulsion triggers removal, not compliance. Government can only remove nodes, not control them. Network continues operating with remaining nodes. Organizations become less valuable targets.
Protection: NUC maps physically unforgeable (atomic-scale manufacturing variance). Attack cost: $100K-1M per camera (destructive hardware analysis). Manufacturer validates against production records.
Complementary, Not Competitive:
Key Differentiator:
"Implement Birthmark alongside C2PA for comprehensive authentication. C2PA handles rich metadata and existing workflows. Birthmark handles the 95% of images that lose metadata through social media sharing."