

A system that proves photos came from real cameras, not AI generators. By creating unforgeable digital signatures at the moment of capture and recording them on a blockchain operated by a coalition of journalism and fact-checking organizations, we're restoring trust in photography.
AI-generated images are increasingly indistinguishable from real photographs, creating a crisis of trust in visual media.
Existing solutions like C2PA rely on metadata that's easily removed through format conversion, cropping, or screenshotting.
Professional photographers' legitimate work is dismissed as fake, undermining journalism, legal evidence, and democratic discourse.
A hash converts data of any size into a fixed-length unique fingerprint. The same input always produces the same hash, but even the tiniest change creates a completely different one. Critically, you cannot convert a hash back into the original data.
Example: An image produces hash "a3f2b8...". Change one pixel, and you get an entirely different hash like "d91e4c...".
Encryption scrambles data using a secret key so only authorized parties can decrypt and read it.
Example: Your camera encrypts its identity—only the manufacturer with the decryption key can verify it's legitimate.
Blockchain is a permanent, tamper-proof public ledger. Once data is recorded on a blockchain, it cannot be changed or deleted—even if companies go out of business or try to censor records.
Example: When your photo's hash is recorded on the Birthmark blockchain, that record is permanent and publicly verifiable by anyone, forever. The blockchain is operated by trusted institutions like universities and archives.
At the moment of image capture, a secure chip in the camera creates an unforgeable digital signature before the image is even processed.
Result: A bundle containing both image hashes, timestamp, and optional location hash—ready to be sent to the aggregation server for validation and blockchain recording.
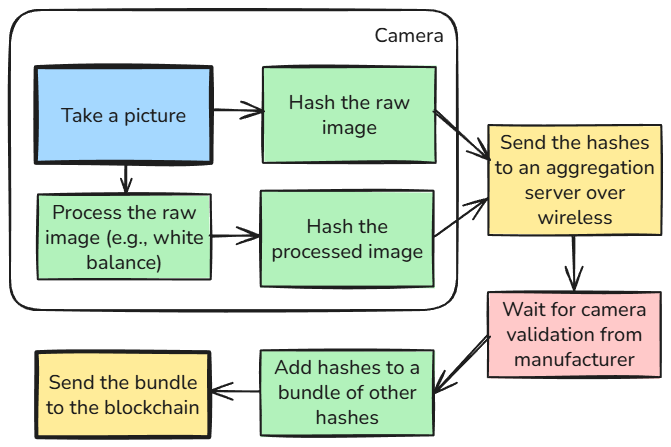
Click to view full size
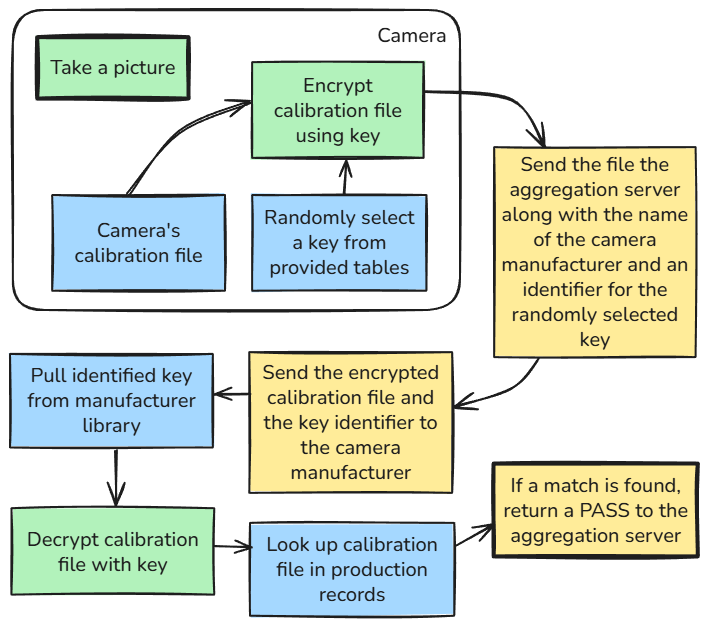
Click to view full size - Shows separation of concerns: manufacturer validates camera, never sees image content
The manufacturer confirms that images come from real cameras without being able to see what photographers are capturing or track individual cameras.
Anyone can verify an image's authenticity by checking the blockchain record—no corporate gatekeepers or subscription services required.
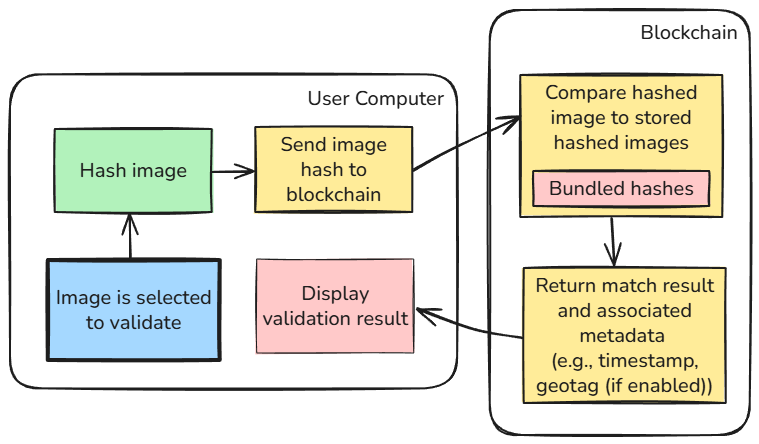
Click to view full size - User verification happens client-side
Deep dive into the cryptographic foundations, system components, privacy guarantees, and security model.
Coalition membership, node ownership, voting structure, and the legal framework that makes the system censorship-resistant.
All code is open source under Apache License 2.0. Explore the implementation, contribute, or deploy your own node.
Fully transparent system—no corporate secrets or proprietary control.
Anonymous camera identifiers prevent tracking while maintaining authentication integrity.
Records survive even if companies go bankrupt or images are cropped and reposted.
No gas fees or transaction costs—institutional validators donate hosting as a public good.
C2PA provides rich metadata embedded in files. Birthmark provides independent blockchain verification that survives when metadata gets stripped by social media.
Anyone can run servers—no single point of control or censorship.
Legal compulsion triggers node removal, not compliance. Governments cannot subvert the network—only remove individual nodes from it.